
NSE4_FGT-6.0 Exam Questions & Answers
Exam Code: NSE4_FGT-6.0
Exam Name: Fortinet NSE 4 - FortiOS 6.0
Updated:
Q&As: 126
At Passcerty.com, we pride ourselves on the comprehensive nature of our NSE4_FGT-6.0 exam dumps, designed meticulously to encompass all key topics and nuances you might encounter during the real examination. Regular updates are a cornerstone of our service, ensuring that our dedicated users always have their hands on the most recent and relevant Q&A dumps. Behind every meticulously curated question and answer lies the hard work of our seasoned team of experts, who bring years of experience and knowledge into crafting these premium materials. And while we are invested in offering top-notch content, we also believe in empowering our community. As a token of our commitment to your success, we're delighted to offer a substantial portion of our resources for free practice. We invite you to make the most of the following content, and wish you every success in your endeavors.

Download Free Fortinet NSE4_FGT-6.0 Demo
Experience Passcerty.com exam material in PDF version.
Simply submit your e-mail address below to get started with our PDF real exam demo of your Fortinet NSE4_FGT-6.0 exam.
![]() Instant download
Instant download
![]() Latest update demo according to real exam
Latest update demo according to real exam
* Our demo shows only a few questions from your selected exam for evaluating purposes
Free Fortinet NSE4_FGT-6.0 Dumps
Practice These Free Questions and Answers to Pass the NSE4 Exam
Which of the following statements about policy-based IPsec tunnels are true? (Choose two.)
A. They can be configured in both NAT/Route and transparent operation modes.
B. They support L2TP-over-IPsec.
C. They require two firewall policies: one for each directions of traffic flow.
D. They support GRE-over-IPsec.
Which of the following are purposes of NAT traversal in IPsec? (Choose two.)
A. To detect intermediary NAT devices in the tunnel path.
B. To dynamically change phase 1 negotiation mode aggressive mode.
C. To encapsulation ESP packets in UDP packets using port 4500.
D. To force a new DH exchange with each phase 2 rekey.
When using WPAD DNS method, which FQDN format do browsers use to query the DNS server?
A. srv_proxy.
B. srv_tcp.wpad.
C. wpad.
D. proxy.
Examine the IPS sensor and DoS policy configuration shown in the exhibit, then answer the question below.
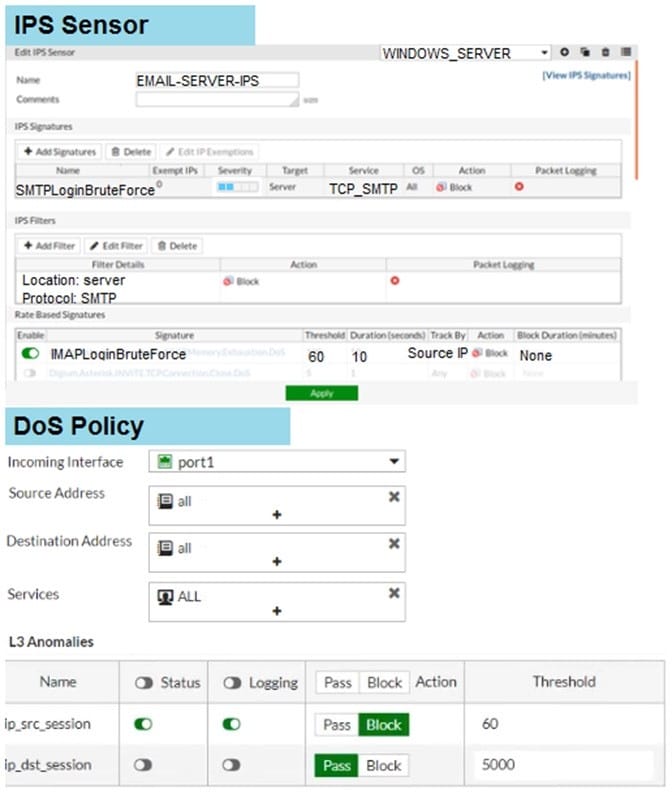
When detecting attacks, which anomaly, signature, or filter will FortiGate evaluate first?
A. SMTP.Login.Brute.Force
B. IMAP.Login.brute.Force
C. ip_src_session
D. Location: server Protocol: SMTP
View the exhibit.
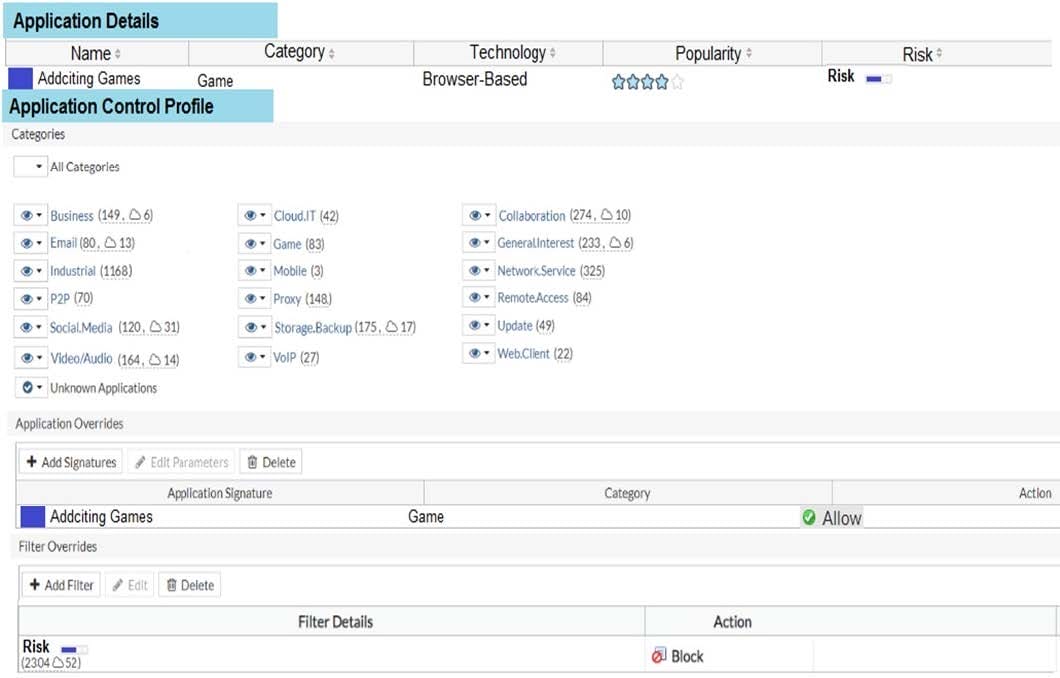
A user behind the FortiGate is trying to go to http://www.addictinggames.com (Addicting Games). Based on this configuration, which statement is true?
A. Addicting.Games is allowed based on the Application Overrides configuration.
B. Addicting.Games is blocked on the Filter Overrides configuration.
C. Addicting.Games can be allowed only if the Filter Overrides actions is set to Learn.
D. Addcting.Games is allowed based on the Categories configuration.
Viewing Page 1 of 3 pages. Download PDF or Software version with 126 questions

