
NSE4_FGT-6.2 Exam Questions & Answers
Exam Code: NSE4_FGT-6.2
Exam Name: Fortinet NSE 4 - FortiOS 6.2
Updated: Jul 10, 2023
Q&As: 142
At Passcerty.com, we pride ourselves on the comprehensive nature of our NSE4_FGT-6.2 exam dumps, designed meticulously to encompass all key topics and nuances you might encounter during the real examination. Regular updates are a cornerstone of our service, ensuring that our dedicated users always have their hands on the most recent and relevant Q&A dumps. Behind every meticulously curated question and answer lies the hard work of our seasoned team of experts, who bring years of experience and knowledge into crafting these premium materials. And while we are invested in offering top-notch content, we also believe in empowering our community. As a token of our commitment to your success, we're delighted to offer a substantial portion of our resources for free practice. We invite you to make the most of the following content, and wish you every success in your endeavors.

Download Free Fortinet NSE4_FGT-6.2 Demo
Experience Passcerty.com exam material in PDF version.
Simply submit your e-mail address below to get started with our PDF real exam demo of your Fortinet NSE4_FGT-6.2 exam.
![]() Instant download
Instant download
![]() Latest update demo according to real exam
Latest update demo according to real exam
* Our demo shows only a few questions from your selected exam for evaluating purposes
Free Fortinet NSE4_FGT-6.2 Dumps
Practice These Free Questions and Answers to Pass the NSE4 Exam
View the exhibit.
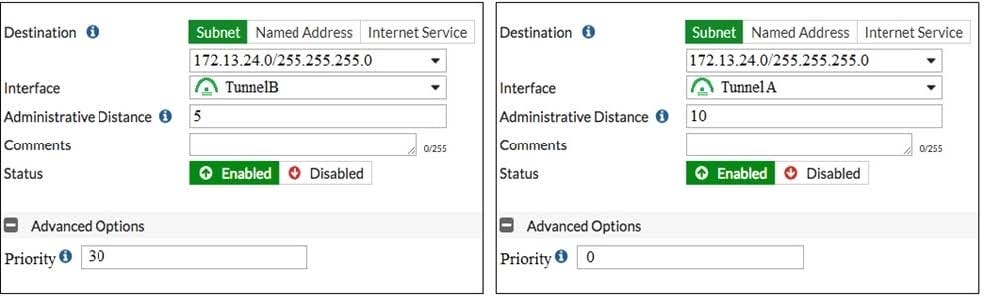
Which of the following statements are correct? (Choose two.)
A. This setup requires at least two firewall policies with the action set to IPsec.
B. Dead peer detection must be disabled to support this type of IPsec setup.
C. The TunnelB route is the primary route for reaching the remote site. The TunnelA route is used only if the TunnelB VPN is down.
D. This is a redundant IPsec setup.
View the exhibit.
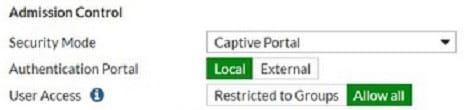
Which users and user groups are allowed access to the network through captive portal?
A. Users and groups defined in the firewall policy.
B. Only individual users ?not groups ?defined in the captive portal configuration
C. Groups defined in the captive portal configuration
D. All users
An administration wants to throttle the total volume of SMTP sessions to their email server. Which of the following DoS sensors can be used to achieve this?
A. tcp_port_scan
B. ip_dst_session
C. udp_flood
D. ip_src_session
Which of the following statements are best practices for troubleshooting FSSO? (Choose two.)
A. Include the group of guest users in a policy.
B. Extend timeout timers.
C. Guarantee at least 34 Kbps bandwidth between FortiGate and domain controllers.
D. Ensure all firewalls allow the FSSO required ports.
Which is the correct description of a hash result as it relates to digital certificates?
A. A unique value used to verify the input data
B. An output value that is used to identify the person or device that authored the input data.
C. An obfuscation used to mask the input data.
D. An encrypted output value used to safe-guard the input data
Viewing Page 1 of 3 pages. Download PDF or Software version with 142 questions

