
PCDRA Exam Questions & Answers
Exam Code: PCDRA
Exam Name: Palo Alto Networks Certified Detection and Remediation Analyst
Updated:
Q&As: 91
At Passcerty.com, we pride ourselves on the comprehensive nature of our PCDRA exam dumps, designed meticulously to encompass all key topics and nuances you might encounter during the real examination. Regular updates are a cornerstone of our service, ensuring that our dedicated users always have their hands on the most recent and relevant Q&A dumps. Behind every meticulously curated question and answer lies the hard work of our seasoned team of experts, who bring years of experience and knowledge into crafting these premium materials. And while we are invested in offering top-notch content, we also believe in empowering our community. As a token of our commitment to your success, we're delighted to offer a substantial portion of our resources for free practice. We invite you to make the most of the following content, and wish you every success in your endeavors.

Download Free Palo Alto Networks PCDRA Demo
Experience Passcerty.com exam material in PDF version.
Simply submit your e-mail address below to get started with our PDF real exam demo of your Palo Alto Networks PCDRA exam.
![]() Instant download
Instant download
![]() Latest update demo according to real exam
Latest update demo according to real exam
* Our demo shows only a few questions from your selected exam for evaluating purposes
Free Palo Alto Networks PCDRA Dumps
Practice These Free Questions and Answers to Pass the Palo Alto Networks Certification Exam
What license would be required for ingesting external logs from various vendors?
A. Cortex XDR Pro per Endpoint
B. Cortex XDR Vendor Agnostic Pro
C. Cortex XDR Pro per TB
D. Cortex XDR Cloud per Host
In Windows and macOS you need to prevent the Cortex XDR Agent from blocking execution of a file based on the digital signer. What is one way to add an exception for the singer?
A. In the Restrictions Profile, add the file name and path to the Executable Files allow list.
B. Create a new rule exception and use the singer as the characteristic.
C. Add the signer to the allow list in the malware profile.
D. Add the signer to the allow list under the action center page.
What is the purpose of targeting software vendors in a supply-chain attack?
A. to take advantage of a trusted software delivery method.
B. to steal users' login credentials.
C. to access source code.
D. to report Zero-day vulnerabilities.
Which statement is correct based on the report output below?
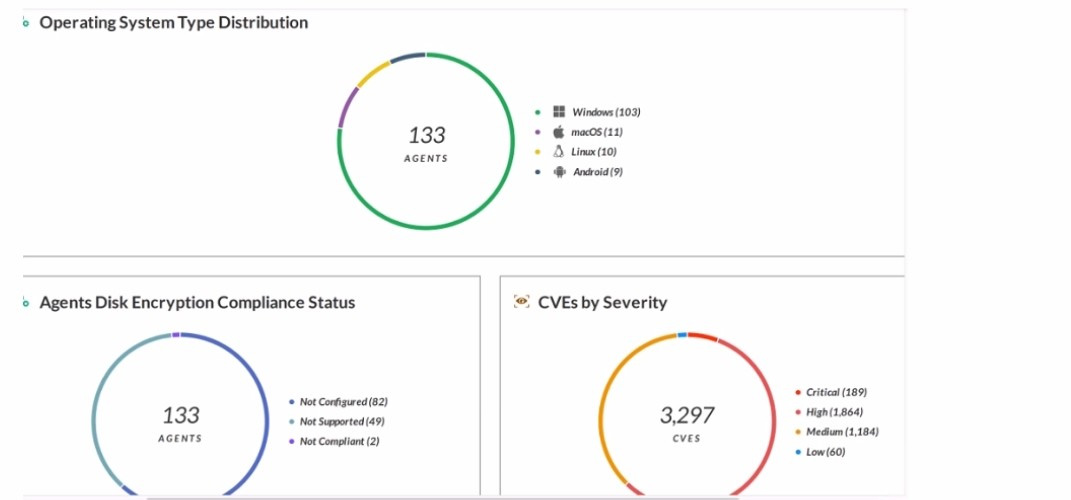
A. Host Inventory Data Collection is enabled.
B. 3,297 total incidents have been detected.
C. Forensic inventory data collection is enabled.
D. 133 agents have full disk encryption.
As a Malware Analyst working with Cortex XDR you notice an alert suggesting that there was a prevented attempt to download Cobalt Strike on one of your servers. Days later, you learn about a massive ongoing supply chain attack. Using Cortex XDR you recognize that your server was compromised by the attack and that Cortex XDR prevented it. What steps can you take to ensure that the same protection is extended to all your servers?
A. Create Behavioral Threat Protection (BTP) rules to recognize and prevent the activity.
B. Enable DLL Protection on all servers but there might be some false positives.
C. Create IOCs of the malicious files you have found to prevent their execution.
D. Enable Behavioral Threat Protection (BTP) with cytool to prevent the attack from spreading.
Viewing Page 1 of 3 pages. Download PDF or Software version with 91 questions

