
SC-900 Exam Questions & Answers
Exam Code: SC-900
Exam Name: Microsoft Security Compliance and Identity Fundamentals
Updated: Dec 18, 2024
Q&As: 233
At Passcerty.com, we pride ourselves on the comprehensive nature of our SC-900 exam dumps, designed meticulously to encompass all key topics and nuances you might encounter during the real examination. Regular updates are a cornerstone of our service, ensuring that our dedicated users always have their hands on the most recent and relevant Q&A dumps. Behind every meticulously curated question and answer lies the hard work of our seasoned team of experts, who bring years of experience and knowledge into crafting these premium materials. And while we are invested in offering top-notch content, we also believe in empowering our community. As a token of our commitment to your success, we're delighted to offer a substantial portion of our resources for free practice. We invite you to make the most of the following content, and wish you every success in your endeavors.

Download Free Microsoft SC-900 Demo
Experience Passcerty.com exam material in PDF version.
Simply submit your e-mail address below to get started with our PDF real exam demo of your Microsoft SC-900 exam.
![]() Instant download
Instant download
![]() Latest update demo according to real exam
Latest update demo according to real exam
* Our demo shows only a few questions from your selected exam for evaluating purposes
Free Microsoft SC-900 Dumps
Practice These Free Questions and Answers to Pass the Fundamentals Exam
What can you specify in Microsoft 365 sensitivity labels?
A. how long files must be preserved
B. when to archive an email message
C. which watermark to add to files
D. where to store files
You have a Microsoft 365 tenant that uses trainable classifiers.
You are creating a custom trainable classifier.
You collect 300 sample file types from various geographical locations to use as seed content. Some of the file samples are encrypted.
You organize the files into categories as shown in the following table.
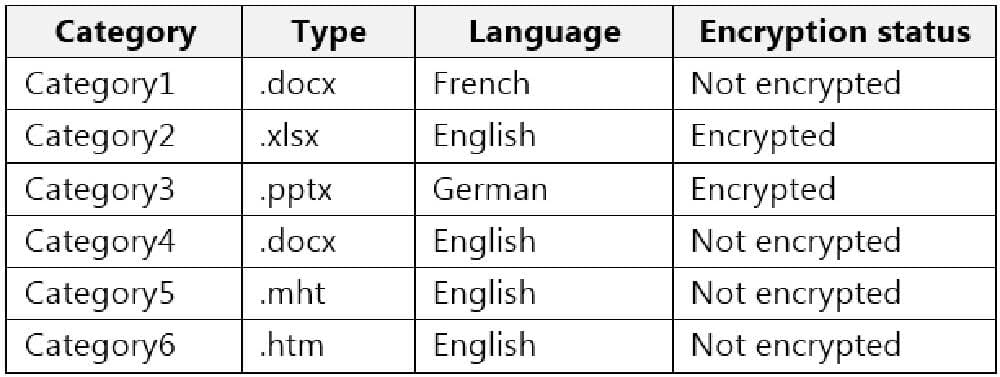
Which file categories can be used as seed content?
A. Category2, Category3, and Category5 only
B. Category1 and Category3 only
C. Category4 and Category6 only
D. Category4 and Category5 only
What should you use to ensure that the members of an Azure Active Directory group use multi-factor authentication (MFA) when they sign in?
A. Azure Active Directory (Azure AD) Identity Protection
B. a conditional access policy
C. Azure role-based access control (Azure RBAC)
D. Azure Active Directory (Azure AD) Privileged Identity Management (PIM)
Which three tasks can be performed by using Azure Active Directory (Azure AD) Identity Protection? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. Configure external access for partner organizations.
B. Export risk detection to third-party utilities.
C. Automate the detection and remediation of identity based-risks.
D. Investigate risks that relate to user authentication.
E. Create and automatically assign sensitivity labels to data.
Which Microsoft Defender for Cloud metric displays the overall security health of an Azure subscription?
A. resource health
B. secure score
C. the status of recommendations
D. completed controls
Viewing Page 1 of 3 pages. Download PDF or Software version with 233 questions

